Digital Photography Headline Animator
Tuesday, 15 November 2011
Web Development Articles
 Implementing New Technology
Implementing New Technology
There are amusing and horrific stories of the trials and tribulations associated with the transfer of technology, and the implementation of new systems and architecture. There are lessons that we can learn from those who have blazed the trails before us, and those who have been burned by the blaze. Get your fingers ready to count the five fundamental considerations for implementing new technology.
 XHTML - Kicking And Screaming Into The Future
XHTML - Kicking And Screaming Into The Future
XHTML, the standard, was first released back in 2000. Roughly five years later we begin to see major websites revised to use this standard. Even the favorite whipping boy of standards-compliance punditry, Microsoft, presents their primary homepages, msn.com and microsoft.com in XHTML. Standards compliant XHTML sites are still the minority. The reason is simple. When the W3C released the new standard, the rest of the web running on HTML did not cease to function. Nor will the rest of the web, ...
 Rich Internet Applications: Has Microsoft Finally Seen the (Silver) Light?
Rich Internet Applications: Has Microsoft Finally Seen the (Silver) Light?
What Are Rich Internet Applications? Rich Internet applications provide an end user with an interface that is more responsive than traditional applications. Many of the frameworks used to create these applications, including both Microsoft Silverlight and Flex, bring more of the processing to the client rather than leaving it on a centralized server. The user's browser does not exchange large, monolithic blocks of information, but rather sends small pieces of data at a ...
 How To Get Quality Web Content
How To Get Quality Web Content
The Importance of Quality Web Content - And How To Get It. Search engine optimization is crucial to get traffic to your membership site. You likely already know this because it's difficult to avoid. Everyone and their brother has an idea about how to best go about getting your membership site listed high on the search engines. The truth is actually much simpler. The truth is that content always has been and is still the key to search engine optimization.
 Web 2.0 Concepts to Keep Your Members Coming Back
Web 2.0 Concepts to Keep Your Members Coming Back
Web 2.0 Concepts to Keep Your Members Coming Back Again and Again and AgainWeb 2.0 may be the most overused, and misunderstood, term of the decade. What it means, in a nutshell is providing a user driven website. Basically many membership marketing websites are Web 2.0, especially social networking sites. The users determine the content in the form of forums, blogs, article posting, reviews and so on. To further enhance the usability of your website and thus the benefit to your members, ...
 40 Simple Ways to Build Trust in Your Website Visitors
40 Simple Ways to Build Trust in Your Website Visitors
Let me start this article by asking a simple question to you. If you give contract to build your home, to whom you will give? Someone new or someone who is trusted by your close friend or relative? Of course the answer is someone trustworthy person/company by you directly or by someone in whom you trust (your friends/relatives). As you know that 'Trust' is really important in life and that's what exactly I want to mention here to bring success in your website. As a business person, remember ...
 Top 10 Application Security Vulnerabilities in Web.config Files - Part Two
Top 10 Application Security Vulnerabilities in Web.config Files - Part Two
An additional problem is that Web.config files were designed to be changed at any time, even after the Web-based applications are in production. A well-intentioned system administrator could inadvertently get around application security measures and open the Web site to attack just by modifying the configuration file. And because .NET configuration files operate in a hierarchical manner, a single change to the global Machine.config file could affect every Web site on the entire network.
 Preparing for successful and professional online presences
Preparing for successful and professional online presences
As the importance of an internet presence becomes increasingly evident to those offering any form of practices, services, business, or information - the implied question is how to go about obtaining a website designed, developed and promoted to best meet your goals?
 What to choose: web site template or custom development?
What to choose: web site template or custom development?
In our time of rapid development and growth of Internet and Internet technologies more and more companies understand that presence of web site has beneficial influence on development of business. There is no doubt about that, but a question appears: “what should site be to positively influence business and not bring heaps of problems?â€.
 Dynamic Site Design: Keeping Your Pages Uniform
Dynamic Site Design: Keeping Your Pages Uniform
At my company we build dynamic websites - sites which constantly adapt to user input and allow for extensive content management by site administrators. Regardless of the amount of information on a page, the design should adapt, maintaining its professional appearance.
 Learn HTML Through Theft & Mutilation
Learn HTML Through Theft & Mutilation
Anyone serious about having a website needs to know something about HTML, the computer code of websites.
 Auto Redirecting What It Is and How to Use It
Auto Redirecting What It Is and How to Use It
Many web designers are using auto redirecting techniques lately for a number of reasons. Auto redirecting occurs when a visitor to your website is automatically sent to another page when he or she has landed on a given page. This other page is frequently located on the same website but can also be located on an entirely different website.
 Using 301 Redirects
Using 301 Redirects
Before we go any further, you are probably wondering what in the world 301 redirects are in the first place am I right? You've heard the term, heard people asking about it and are curious but it just sounds so technical you aren't sure what to do with it.
 Cooking up a Great Web Site
Cooking up a Great Web Site
The elements of a website; Would you leave out the eggs when making cookies? It is important to add all of the ingredients to a recipe in order for the end result to come out how it should, the same goes for making a website. It is important to have all of your elements in place, i.e. navigation, content, promos etc.Too often I have had clients all wrapped up in the ‘pretty’ and look of thiee site and not the ...
 Web Accessibility: Web Design for the Mobility-Impaired
Web Accessibility: Web Design for the Mobility-Impaired
Mobility impairment isn’t always as obvious as you might think it is. You don’t have to imagine extremes of disability like paralysis or missing limbs. Try imagining a simple fall or other accident that results in both hands in a cast and unable to use a mouse. Now, with that in mind, open your website in your browser, put an unsharpened pencil in your mouth, and try to use the eraser to push the TAB key till you get all the way to the main content of your page. With a properly placed ...
 Web Accessibility: WCAG 2.0 and You
Web Accessibility: WCAG 2.0 and You
We interrupt our irregularly scheduled series on web accessibility for a not so late breaking news flash (sans Flash, of course.) It seems that the W3C (World Wide Web Consortium) is on the verge of releasing a whole new set of Web Content Accessibility Guidelines called WCAG 2.0. With numerous changes in place, it now seems that the whole set of guidelines that many of us have worked so hard to implement are all kind of up in the air.
 Processes in Website and Application Development
Processes in Website and Application Development
Almost all top most companies engaged in the field of software development follow best practices followed in the field of software engineering.The solution provided by McDaav Systems is based upon the Rational Unified Process and we follow UML 2.0 specification while doing System Analysis.
 Different Ways To Redirect Visitors To Any URL You Want
Different Ways To Redirect Visitors To Any URL You Want
URL redirection can be used for many purposes. Maybe you have just moved the content of a webpage to another webpage or domain and you want to redirect the frequent visitors of your website to the new webpage automatically. The knowledge of technique of redirecting URL is also useful if you want to shorten a long affiliate URL.
 Web Sites... In The Beginning
Web Sites... In The Beginning
For many business areas, the Internet has set a new standard and changed the playing field. To take advantage, you need a site. But where do you start?
 Remembering Your First Internet KISS
Remembering Your First Internet KISS
Do you remember your fist KISS; was it really how you imagined it would be? Well let me continue. If your first kiss was disappointing, was it through lack of knowledge of how a kiss should be, or was it simply your nervousness or anticipation of what was coming that made it such a flop. Your excitement growing more and more, as the moment arrived, your throat drying by the second, hands and knees trembling. Then it was gone in an instant.
 10 Quick Website Maintance Tips
10 Quick Website Maintance Tips
1. Keep all your images in a subfolder. If your file is something.com/index.html, then your images for that should be in something.com/images/
 Introduction To Regular Expressions In PHP
Introduction To Regular Expressions In PHP
In Linux and Unix, the syntax that is commonly used by many applications for specifying text patterns is known as regular expressions or in short form - regex. Regex is a very powerful technique to describe patterns and many programs use them to describe sequences of characters to be matched. Search programs such as 'grep' rely heavily on regex. Basically regex forms the core in the linux world. Many scripting languages such as perl, ruby, php...etc has build in regex functions as ...
 XHTML (eXtended Hypertext Markup Language): An Overview
XHTML (eXtended Hypertext Markup Language): An Overview
Many Web pages today are poorly written. Syntactically incorrect HTML code may work in most browsers even if it doesn't follow HTML rules. Browsers employ heuristics to deal with these flawed Web pages; however, Web-enabled wireless devices (such as PDAs) can't accommodate these hefty Web browsers. The next step in HTML’s evolution comes in the form of XHTML (eXtended Hypertext Markup Language), which is basically a combination of HTML and
 Making a Web Content Site a Media-Friendly One
Making a Web Content Site a Media-Friendly One
It has always been a very tough competition among PR pros to get the attention of the media. In Public Relations, often, professionals are faced with the awful truth that no matter how relevant and good their stories are, many ended up in trash, or worst, others were turned down before they could even start introducing their pitches. In this kind of profession, everyday seemed to be a struggle. If PR pitches are rejected by journalists, the message to be conveyed dies out instantly no matter ...
 Your Home Business Site's Usability Can Increase Your Buyers by 40% and Boost Each Order By 10%!
Your Home Business Site's Usability Can Increase Your Buyers by 40% and Boost Each Order By 10%!
Is your site easy to use? Usability isn't the same as design. Just because you've hired a talented designer to craft your site and make it look great doesn't mean it's easy to use. Looking good is a completely different matter from working well! After all, plenty of beautiful sites have won design awards while losing customers by the thousands.How many times have you gotten lost on a good-looking site or abandoned a purchase in frustration after you couldn't find ...
 XML (eXtensible Markup Language): An Overview
XML (eXtensible Markup Language): An Overview
As web developers know all too well, basic HTML (HyperText Markup Language) doesn't provide any structure to Web pages, and the formatting is mixed with the content. To allow Web pages to be structured for automated processing (e.g. electronic commerce), the World Wide Web Consortium (W3C) developed an enhancement to HTML. The result were two new languages; one was XSL (eXtensible Style Language), and the other was XML (eXtensible Markup Language), a system for defining, ...
 Making your Website Memorable
Making your Website Memorable
To do this you must make your site and company stand out in your prospect's mind. Design your website to impressInformative content to make your visitor thinkProduct and book reviews that will pique curiosity.Hot in demand product and serviceSimple navigation to draw them into your site.Good small graphics aimed to entice.Fat loadingNicely presented font and coloring that does not take ...
 Contracts with Web Site Designers and Hosting Companies
Contracts with Web Site Designers and Hosting Companies
There are many aspects to website development agreement, particularly if there are to be on-going things for the designer to do once the site has been set up. The core issues that should be considered are set out as follows...
 Key Considerations in Web Site Development Agreements
Key Considerations in Web Site Development Agreements
When web developers and their clients get together, there can be a variety of different responses. Some are so keen to get on with the project that they completely ignore the legal contract; others simply work on the standard terms and do not bother looking at them; still others sit down and negotiate an agreement that works for both parties.
 The Brother-in-Law Syndrome Applied to Websites
The Brother-in-Law Syndrome Applied to Websites
The Syndrome This article could have been named “my neighbor down the street†syndrome or “my niece†syndrome. It’s really a “fill in the blank†syndrome that indicates a person’s response to the thought process for developing (or re-developing) a website for your company. This syndrome kicks in when your response is “Oh, my brother-in-law does websites, he can do one for our companyâ€.Have you uttered those words? Do you know of someone who has said ...
SEO Software
Are you looking to increase productivity and reduce the time you spend on repetitive SEO (Search Engine Optimization) tasks? Well, here are six leading SEO software programs, tools and services for Windows, Mac and Linux users to improve their search engine rankings. Typical SEO software features include webpage optimization, submissions to web and article directories, find backlinks from relevant websites, and search engine ranking reports.
| Internet Business Promoter (IBP) is a SEO software program that has been around for a few years now and is up to version 11. The SEO software features include keyword research, top 10 webpage optimizer, search engine spider simulator, inbound link builder, link management, search engine and web directory submission, search engine ranking checker and customizable reports, scheduler, and project management. Internet Business Promoter is the only SEO software solution I know of that offers a 12 month guarantee of top 10 organic (natural) rankings in Google for keywords of your choice or your money back. Maybe that's a marketing gimmick, but it is a good on | ||||||||||||||||||||||||
ISP
ISP
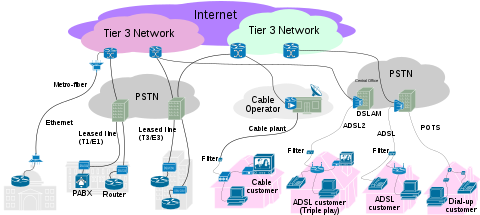 Short for Internet Service Provider, it refers to a company that provides Internet services, including personal and business access to the Internet. For a monthly fee, the service provider usually provides a software package, username, password and access phone number. Equipped with a modem, you can then log on to the Internet and browse the World Wide Web and USENET, and send and receive e-mail.
For broadband access you typically receive the broadband modem
hardware or pay a monthly fee for this equipment that is added to your
ISP account billing.
Short for Internet Service Provider, it refers to a company that provides Internet services, including personal and business access to the Internet. For a monthly fee, the service provider usually provides a software package, username, password and access phone number. Equipped with a modem, you can then log on to the Internet and browse the World Wide Web and USENET, and send and receive e-mail.
For broadband access you typically receive the broadband modem
hardware or pay a monthly fee for this equipment that is added to your
ISP account billing.Shared or Dedicated Server?
There are basically two types of hosting service: shared and dedicated. They differ in terms of performance and price. Their characteristics are as follows:
When you cannot find any information whether the offered hosting services are shared or dedicated, they are most likely shared ones. Dedicated hosting very rarely costs less than $80 a month, so if hosting plans you are interested in are significantly cheaper, they are most definitely shared ones.
- Shared hosting. It's a configuration where several websites are put on on single server. This way the hosting company can reduce its cost, and their services can be much cheaper. However, there are usually much more limits on the storage and bandwidth, because one server must handle several websites at once. You should choose this kind of hosting if your website will not get really many visitors (less than few thousands a day).
- Dedicated hosting. Your website is the only one hosted on the server. You can utilize full hard disk size for your website, you can run scripts which consume lots of CPU power, and you can have many more visitors on your website. You should choose this type of hosting if you plan to run a very popular website, or you have high storage or bandwidth requirements (for example, site with free downloads).
Potential Disadvantages of Dedicated Hosting
Before signing up for dedicated
server hosting, there are some factors you should consider. There are
some potential disadvantages to dedicated hosting. However, if you can
afford the monthly fees associated with dedicated hosting, the benefits
often outweigh the disadvantages. It is still important to consider any
downsides to dedicated server hosting before making your final decision.
Dedicated hosting is more expensive
than shared hosting services. The cost per month can be as high as $99
and up. While this may not be a problem for many business websites, it
is often too expensive for an individual to pay each month to host their
website. For some websites, such as a hobby website the cost for a
dedicated server is often just too much. For larger websites especially
those for businesses and organizations the price is often more
acceptable.
It is essential that you select an
excellent hosting provider. They will own and maintain your server. The
server will be stored in their own data center so you must depend upon
the host to maintain your server and all their hosting equipment well.
If you select a host who is not very reliable, you can have serious
problems with your hosting experience. You could find that your website
is not line or not functioning as you need it to function. This can also
happen with shared hosting of course. However, a hosting client is
paying a great deal more for dedicated server hosting and should have a
relatively worry free hosting experience.
If you have unmanaged dedicated
hosting, your hosting services can take up a great deal of time and
money to maintain. Administrating tasks on a server can be very
difficult especially if you have very little technical training and
knowledge. For this reason you will need one or more people on staff who
have the technical knowledge necessary to manage your hosting services.
If you do not have an IT staff, that means that whoever works on the
hosting end of your business will not have as much time for other tasks.
When you do not have someone
knowledgeable enough to manage your hosting experience, you will need to
hire an IT person or outsource the work. This will cost your business
money in excess to your dedicated server hosting fees. The costs can add
up quickly when paying someone to deal with the technical end of your
business. It may be more cost effective to consider managed dedicated
hosting. In this instance the web-hosting provider will handle many of
the technical and maintenance tasks.
Another potential disadvantage to
dedicated hosting is that you do not have physical access to the
server. Your web-hosting provider will be responsible for maintaining
the actual server. They will provide security measures to protect your
server and data. And they will be responsible for performing server back
ups. If you have a good host this is not much of a problem. However, if
you would select a host that is not so good you could lose data or have
a service that does not perform as well as expected for the cost.
6 Tips for Better Mobile Security
 The more you do on your mobile device, the more you should be
concerned about its security. This is especially true if you use it for
work. Keep in mind, if your device is configured with your employer’s
email or messaging server, they may already be implementing some of the
security tips we’re going to discuss.
The more you do on your mobile device, the more you should be
concerned about its security. This is especially true if you use it for
work. Keep in mind, if your device is configured with your employer’s
email or messaging server, they may already be implementing some of the
security tips we’re going to discuss.Tip No. 1 - Choose a mobile OS that supports encryption, oh, and use it: If you are truly concerned about the security of your mobile phone or device you should use a mobile operating system (OS) and device that supports hardware-based encryption, such as Apple’s iOS or RIM’s BlackBerry, for both internal and external storage. This means the data stored on it is protected even from the most advanced hacker. Without encryption it’s possible that someone could recover the data on the device even without your lock pin or password.
Full device encryption on current Android devices is limited and varies between manufactures. Motorola Mobility's business-oriented smartphones offers encryption capabilities on Android 2.3. Android 3.x includes an API to help developers offer encryption on tablets, which some currently implement. And in the next year, we should see Android 4.x tablets and smartphones support encryption. WhisperCore is a third-party encryption solution you may want to also keep your eye on. Beta versions are currently available for Nexus S and Nexus One.
Tip No. 2 - Set a lock pin or password: Enabling a password, whether it’s called a pin, passcode, or passphrase, is the first line of defense in protecting your privacy and security. It helps prevent others from picking up your phone or device and snooping around if it becomes lost, stolen, or just left unattended. It’s also usually required if encryption is enabled on the device.
If encryption isn’t supported by the OS you should still definitely require yourself to set a password. Though your data can possibly be recovered by determined individuals without them knowing the password, you’ll at least protect it from the causal snoopers.
Tip No. 3 - Enable auto-wiping of data: Most mobile OSes support automatic wiping of the device’s data after a certain number of incorrect passwords attempts. This is great if encryption isn’t supported by the device but it can actually be just as beneficial for encrypted devices. Because giving others unlimited guesses to your password makes it much more possible that they could get it right, and once that happens the data is decrypted.
Auto-wiping is natively supported by iOS, Windows Phone 7, and BlackBerry.
Android requires the use of a third party app, such as Autowipe or a security app as in the last tip.
Just remember to keep all your data regularly backed up and use a solution that lets you restore the data to a new device in case you can’t find the one you wiped.
Tip No. 4 - Setup remote tracking and management: Before your phone or device gets misplaced or stolen you ought to setup a remote tracking and management solution. Most let you see the device’s GPS location on a map, send audible alerts to help you find it, and display a visual message to tell others how to return it. They typically also let you remotely lock and/or wipe it before someone else gets their hands on it.
For iOS 4.2 or later, Apple provides a free service. For earlier iOS versions there’s the MobileMe service from Apple at $99 a year after the 60 day free trial.
For Android you have to use a third-party app, such as the security apps mentioned in the last tip.
For Windows Phone 7 Microsoft provides the free Windows Live for Mobile service.
For BlackBerry, RIM provides the free BlackBerry Protect service.
Tip No. 5 - Limit Wi-Fi hotspot usage: When you use public Wi-Fi hotspots that aren’t encrypted, all your Internet traffic is transmitted through the air and can be easily intercepted. The most important sites and services, such as banking websites, usually implement their own (HTTPS/SSL) encryption that protects their individual traffic. But most email providers and many social networking sites don’t; thus eavesdroppers can likely capture their passwords and traffic.
On the other hand most 3G, 4G, and other cellular data connections are usually encrypted by the carriers. Plus eavesdropping on these types of connections isn’t as popular. Therefore, when you’re out and about you should try to use the data connection rather unsecured Wi-Fi hotspots.
If you insist on using Wi-Fi hotspots, use those that provide enterprise encryption and 802.1X authentication, such as from T-Mobile and iBahn. Alternatively, consider using a VPN connection to secure your traffic from local eavesdroppers.
Tip No. 6 - Use an antivirus or security app: Viruses, malware, and hacking on mobile devices aren’t a huge issue now but they are becoming more of an issue. You should consider installing a security app to help prevent infections and intrusions. Most AV solutions also offer additional features, such as remote wiping, backup and locating.
Computer Security
 Computer Security
Computer Security
What is Computer Security? Computer Security is a branch of technology known as information security as applied to computers. Information security means protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction. The objective of computer security varies and can include protection of information from theft or corruption, or the preservation of availability, as defined in the security policy.
 Top 10 Application Security Vulnerabilities in Web.config Files - Part One
Top 10 Application Security Vulnerabilities in Web.config Files - Part One
These days, the biggest threat to an organization's network security comes from its public Web site and the Web-based applications found there. Unlike internal-only network services such as databases-which can be sealed off from the outside via firewalls-a public Web site is generally accessible to anyone who wants to view it, making application security an issue. As networks have become more secure, vulnerabilities in Web applications have inevitably attracted the attention of hackers, both ...
 Securing your network, from home users to small business up to enterprise. What you can do.
Securing your network, from home users to small business up to enterprise. What you can do.
With computers being a critical component in running a business, it is more valuable than ever to ensure the security of your networks particularly where there is sensitive data. News headlines announcing that networks have experienced security breaches are all too prevalent. This is where you need a service that checks for those vulnerabilities and prevents from future attacks. Better yet, you need a service that prevents it before it ever happens to your company. Imagine the embarrassment at ...
 What Is Malware?
What Is Malware?
You have probably heard computer people talk about Malware and the damage it can cause. I recently realized that those outside the computer industry are not always familiar with the word. So here is my answer to the frequent question, "What is Malware?"
 WLAN security
WLAN security
What about security for WLAN? Today wireless networks are at least secure as wired. You only have to use right tools and configurations. Physical security is most important part of security. If you do not have physical access to network, you can not use it. If you can not plug cable you do not have network. This is situation in wired word.
 Botnets: The Story of How My PC Became a Zombie!
Botnets: The Story of How My PC Became a Zombie!
Several weeks ago, I received a call from my ISP's Security Department. The lady, who was a little short on etiquette, launched into this short story about having to suspend my account due to the fact that someone had hijacked my email login and password. Well, I was at that time not on the Internet but was at my desk so I cranked up the old PC and hit connect on my DSL icon. Well, that's as far as I got: there was no way I was going to connect using my ISP's icon.
 Top Tips for Avoiding Internet Fraud and Scams
Top Tips for Avoiding Internet Fraud and Scams
As ever more people use the internet for shopping, business transactions, online banking, etc., the incidence of internet fraud and scams has shot up in an alarming fashion. Not only has the level of internet crime increased but the scammers and fraudsters grow cleverer and more sophisticated every day. What can you do to fight back? In this article I will describe the most common scams of today so that you can recognize them for yourself and I will suggest how you might deal with them. ...
 What are SSL Certificates?
What are SSL Certificates?
What are SSL Certificates? SSL certificate is the short form of secure socket layer certificate. This technology is used widely in the Internet transactions to make them secure. Normally, this technology is used to encrypt important information between the web servers and the client’s web browser by establishing an encrypted and secure link. This helps in making the information of the transaction private and secure. Millions of Internet transactions that happen everyday are using ...
 Fastest Method To Infect Your Pc With Spyware And Adware
Fastest Method To Infect Your Pc With Spyware And Adware
You follow this advice and you eliminate 90% of the risk involved with adware and spyware infections.
 Computer Security, Viruses And Threats.
Computer Security, Viruses And Threats.
Today, many people rely on computers to do homework, work, and create or store useful information. Therefore, it is important for the information on the computer to be stored and kept properly. It is also extremely important for people on computers to protect their computer from data loss, misuse, and abuse. For example, it is crucial for businesses to keep information they have secure so that hackers can't access the information. Home users also need to take means to make sure that their ...
 SSL: Site Security And Privacy
SSL: Site Security And Privacy
Netscape began using Secure Socket Layer (SSL) in 1994 as a means of sending sensitive data over the web. The newer edition of the service is called Transport Layer Security (TLS), although even this is routinely known by the SSL designation.
 The 10 Minute Secure PC
The 10 Minute Secure PC
With all of the viruses, worms, and spyware floating around in cyberspace it is more important than ever to be security conscious. Securing your PC from all of those nasty programs will not only save you a lot of time, it is also a necessity to help avoid losing important data and potential theft of personal information.
 “Phishing†on the “Pharmâ€: How Thieves Combine Two Techniques to Steal Your Identity
“Phishing†on the “Pharmâ€: How Thieves Combine Two Techniques to Steal Your Identity
Bob squinted at the email and began to read: “Dear eBay User, as part of our security measures, eBay Inc. has developed a security program against fraudulent attempts and account thefts. Therefore, our system requires further account verification…â€
 Hacking: An Inside Job?
Hacking: An Inside Job?
"Leaving your Web applications insecure makes no more sense than building a brick wall but using a gate made from chain link fencing." – James Gaskin
 The Two Things You Must Know About Your Private Information Before It's Too Late
The Two Things You Must Know About Your Private Information Before It's Too Late
Our society is maintained by information: information about who we were, who we are, and in some cases who we will become. We live in the Information age, a time where movement of information is faster than physical movement. Some say that we live in a new type of society called an Information Society, in which the creation, distribution and manipulation of information has become a significant economic and cultural activity. Matthew Lesko, a columnist, made this point clear when he wrote, ...
 Smelling A Hoax A Mile Away By Using A Little Common Sense
Smelling A Hoax A Mile Away By Using A Little Common Sense
It is amazing how quickly the world knew in September 2001 that America was under attack, but years after discovering that a specific e-mail is a hoax, people still don’t know about it. The main problem for this is that people don’t really take the time and effort to inform others about the hoax and like I said, most of these e-mails come from friends and family and it is not always that easy telling these people that it is a hoax, some may feel embarrassed and react negatively to your ...
 Home Network Security Revealed
Home Network Security Revealed
Some home computer users have become experts without knowing it. Just a short time ago terms such as "wireless" and "router" were only known by computer professionals and experts. Not so any more. These days switches, hubs, Ethernet cards, firewalls, routers, and other buzzwords related to networking have become common in many homes.
 The 10 Most Rampant Computer Viruses
The 10 Most Rampant Computer Viruses
Every day new computer viruses are created to annoy us and to wreak havoc on our computer systems. Below are ten viruses currently cited as being the most prevalent in terms of being seen the most or in their ability to potentially cause damage. New viruses are created daily. This is by no means an all inclusive list. The best thing you can do is to remain vigilant, keep your anti-virus software updated, and stay aware of the current computer virus threats.
 Virus Hoaxes - As Bad As The Real Thing?
Virus Hoaxes - As Bad As The Real Thing?
A computer virus can cause a great deal of damage to your computer or can lead to the theft of your data. This can result in programs that don't work, real time money that is stolen, and time that is lost.
 Online Shopping Safety...What about Passwords
Online Shopping Safety...What about Passwords
Enhance Your Online Shopping Experience The annual shopping season is just around the corner. This can be a very exciting time, depending on your perspective, it could be fun or just a real pain. For those that would rather avoid the crowds, traffic and the occasional rude shopper, here are a few comments to consider:Passwords Are Such A Pain! Most of us consider passwords a pain in the butt. I did too until I started to think. Just imagine what could happen if ...
 Computer Viruses - Learn To Keep Your Computer Safe
Computer Viruses - Learn To Keep Your Computer Safe
A virus is computer code that somehow finds its way into your computer without your knowledge. It interacts with your computer's operating system and memory and does troublseome things in your computer, often without your knowledge. Most people don't even know they have been infected by a virus until, all of a sudden, their computer slows down to a crawl or doesn't work at all. This happens when the virus is using all the available memory that used to be used to run your ...
 Security Issues And The Internet
Security Issues And The Internet
With the age of the personal computer upon us, we must be constantly monitoring the activity of children on the Internet. The World Wide Web is filled with an abundance of unsafe sites that children certainly should not have access to. It is rather unfortunate that many parents simply do not have the knowledge about computers with which to implement proper security systems that restrict the Internet content available for the viewing of young children. In not knowing how to restrict the websites ...
 The Biggest Internet Scam In Recent History.
The Biggest Internet Scam In Recent History.
Are you interested in hearing about the biggest internet scam in recent history? NO! Would you be interested if you discovered that it is possibly you that was scammed several months ago and did not even know it? In fact, if you were scammed back then you probably have had money removed from your bank account every month AND you may not even know you are losing your money. Now you are interested!
 Spyware Protection - Backup Software is the Best Defense Against Spyware and Computer Viruses
Spyware Protection - Backup Software is the Best Defense Against Spyware and Computer Viruses
The Worst Case Scenario Your subscriptions to your favorite anti-virus and spyware software expired 28 days ago. You have been meaning to pull out your credit card and renew. However, you just haven't gotten to it.Yesterday an e-mail, SPAM really, hit your inbox with an interesting by-line on the latest natural disaster. You click on the innocuous looking link. The next thing you know, Internet Explorer doesn't quite work correctly, followed by a failure of Windows ...
 Social Sites That Protect Teens
Social Sites That Protect Teens
Social networking sites can be a lot of fun. College students like to use Facebook.com to connect and build relationships. Teenagers and young college students think Myspace.com is the place to be. Networking sites can also put you in contact with people who share similar interests or who are just plain interesting.
 Simple Steps To Protect Your Personal Information From Hackers
Simple Steps To Protect Your Personal Information From Hackers
The Internet is an unlimited sea of information. The user can find information about virtually everything, tangible and intangible, on the web. But, in the cyber world, while users browse various resources for information, there are other unscrupulous blokes who secretly access the personal information of others without their knowledge. Such people who clandestinely breach into other’s private space are technically termed as Hackers.
 How To Avoid Phishing Scams
How To Avoid Phishing Scams
In today’s world the Internet is becoming as common as sliced bread. Most people use it to send e-mails, browse for information, carry out banking transactions, and shop. So it shouldn’t be a surprise that some people are embracing the technology for less-than-kosher purposes. Phishing scams in particular are a major concern. Luckily, if you want to avoid becoming the next victim of identity theft, there are ways to protect yourself from harm.
 Strong Passwords - Meaningful Symbols Increase Password Strength
Strong Passwords - Meaningful Symbols Increase Password Strength
In today’s online world, having a strong password is a must. However, the problem with strong passwords is that they can be difficult to remember. Altering the passwords you currently use by adding a meaningful symbol is one step toward making them difficult for Internet thieves to crack. Here is a list of symbols, some suggested uses, and some examples of how to incorporate them into your passwords:
 Computer Security Ethics and Privacy
Computer Security Ethics and Privacy
Today, many people rely on computers to do homework, work, and create or store useful information. Therefore, it is important for the information on the computer to be stored and kept properly. It is also extremely important for people on computers to protect their computer from data loss, misuse, and abuse. For example, it is crucial for businesses to keep information they have secure so that hackers can’t access the information. Home users also need to take means to make sure that their ...
 Delete Cookies
Delete Cookies
What are cookies? The cookies are small pieces of information (text) that are created by Web sites that you are visiting and are send to your browser (Internet Explorer) along with the Web pages that you are viewing. Some of these cookies are saved to your hard disk and when you visit again the Web site that generated them your browser sends these cookies back to this Web site.The purpose of the cookies is one of the following things:To notify the Web site that you visited it in ...
Subscribe to:
Comments (Atom)
